The Great Data Heist
In the fourth part of The New Feudalism, a whistleblower comes forward with dramatic evidence and a stunning plot twist.
This is part four of our multi-part investigation. Read Part 1 here, Part 2 here, and Part 3 here.
Throughout this series, we've tracked the emergence of a digital feudal system—where Data Lords gain unprecedented access to Americans' most sensitive information while citizens become transparent Data Serfs. We've documented DOGE's systematic capture of government databases, detailed the intimate personal information being collected, and shown how the surveillance net is tightening from our borders to our homes, eventually ensnaring everything we once considered private.
We've all felt powerless to stop it—it just seemed inevitable that net would consume us all watching as the mesh grew finer, the grip tighter—until a single voice spoke out. On National Public Radio. A voice that, against all odds, achieved the impossible - he pierced through the net.
What this whistleblower has uncovered changes everything.
Daniel Berulis isn't a seasoned government whistleblower or political operative. He's an ordinary IT professional who had only been working at the NLRB for about six months before the Trump administration took office. Prior to joining the government, he spent years as a technical consultant, specializing in auditing and modernizing corporate systems. A Midwest transplant with a modest home in the Washington, D.C. suburbs, Berulis had just moved to the area with his dog, still getting settled in his new neighborhood when he found himself at the center of a national security crisis.
"When I first started, it was a dream come true," he told NPR. "There was a great opportunity to build up and do some good." Instead of fulfilling that dream, he found himself facing an impossible choice between his career and his conscience.
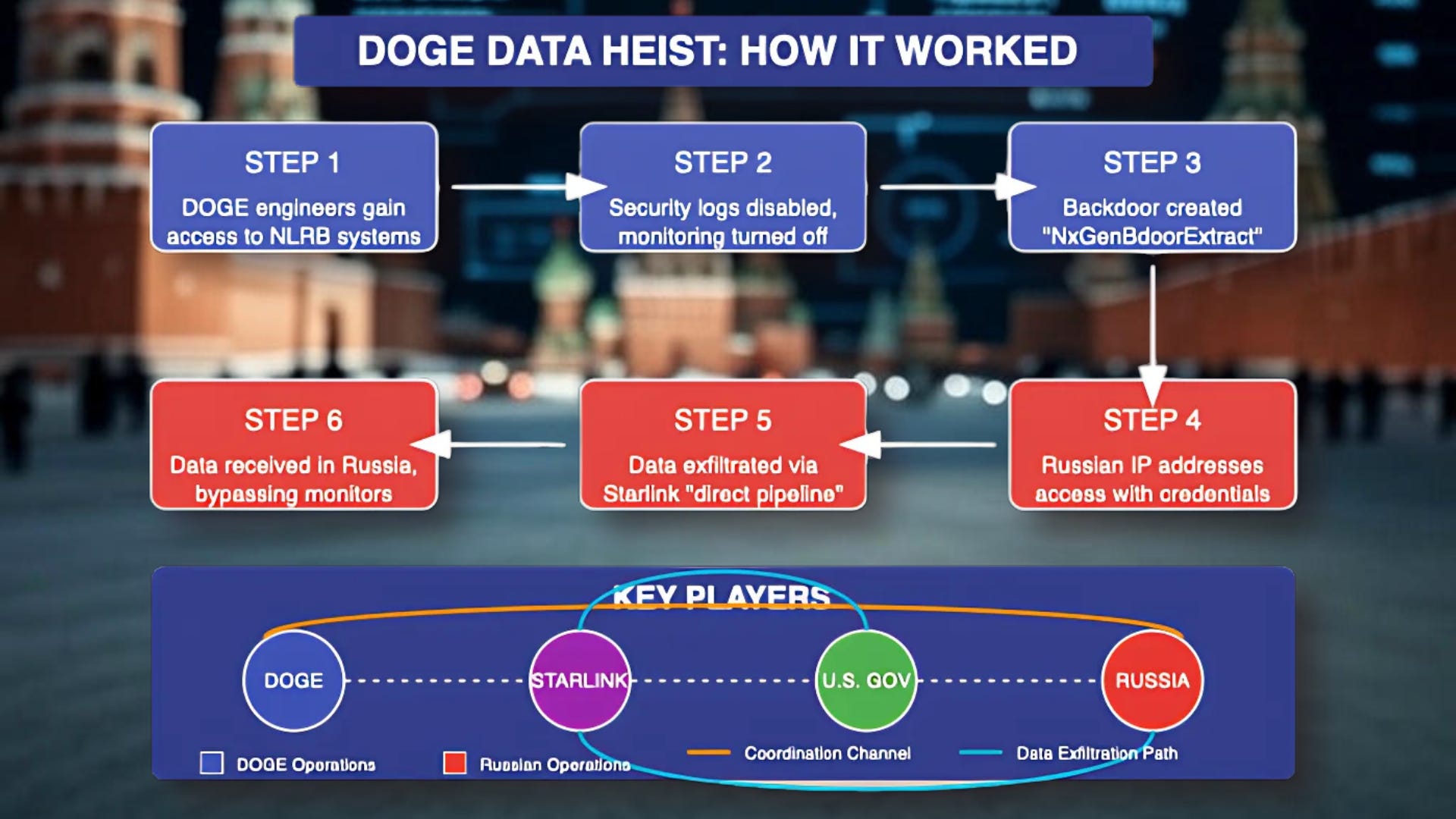
Berulis came forward with explosive evidence: Russian actors accessed U.S. government systems through DOGE, using Elon Musk's Starlink as a "direct pipeline" for data extraction to Russia.
This isn't speculation or partisan rhetoric. It's documented in forensic evidence, sworn testimony, and confirmed by cybersecurity experts who reviewed the whistleblower's claims.
The Whistleblower's Evidence
Berulis was at work when he noticed DOGE engineers gained access to sensitive labor files stored on a secure server. But if that wasn't strange enough, he then spotted someone operating from Russia attempting to log in using newly-created DOGE credentials.
"Within minutes after DOGE accessed the NLRB's systems, someone with an IP address in Russia started trying to log in," Berulis disclosed to NPR. "The attempts were 'near real-time'... Whoever was attempting to log in was using one of the newly created DOGE accounts — and the person had the correct username and password."
This wasn't a random hacking attempt or coincidental timing. As Berulis emphasized, the Russian operatives had the correct login credentials that had just been created. This suggests real-time coordination between DOGE engineers and Russian intelligence.
The evidence goes deeper. Berulis documented that DOGE engineers:
Demanded "tenant-level" access that enabled complete control of NLRB systems
Insisted that their activities not be logged, violating fundamental cybersecurity protocols
Used specialized techniques to mask their actions, including containers that run invisibly
Disabled security controls, removed logs, and bypassed standard monitoring
Created a project named "NxGenBdoorExtract" — suggesting a backdoor to extract files from the NLRB's internal case management system
Former FBI cyber official Russ Handorf, who reviewed Berulis's forensic evidence, confirmed that these techniques match known Russian intelligence tradecraft: "We've seen Russian threat actors do things like this on U.S. government systems."
But the most alarming detail was yet to come.
Starlink: The Direct Pipeline
The smoking gun emerged when Berulis and his attorney Andrew Bakaj appeared on Rachel Maddow's show. Bakaj revealed that DOGE systems "were also connected to Starlink" – Musk's satellite network – which had become "a direct pipeline to Russia."
This revelation transforms our understanding of the breach. Starlink isn't conventional internet infrastructure – it's a satellite network controlled entirely by Elon Musk's SpaceX, operating outside traditional internet pathways and oversight mechanisms.
Unlike standard internet connections that route through multiple providers and leave digital footprints, Starlink's satellites can establish direct links to ground receivers anywhere in the world. This architecture makes it the perfect exfiltration tool: data can be transmitted directly from U.S. government systems to receivers in Russia without passing through the usual monitoring points.
"This type of activity is why the government buys insider-threat-monitoring technology," explained Jake Braun, former White House cyber official. "So we can know things like this are happening and stop sensitive data exfiltration before it happens."
Bakaj further revealed that the Department of Defense had already stopped using Starlink because it's viewed as a "direct pipeline" to Russia. This statement aligns with previous reports that the Pentagon had security concerns about Starlink's vulnerability to foreign compromise.
Bakaj adds Starlink has come up again and again.